Dental Office Compliance in the Age of Cybersecurity and COVID-19
 By Leslie Canham, CDA, RDA, CDIPC, CSP
By Leslie Canham, CDA, RDA, CDIPC, CSP
When it comes to my computer, nothing scares me more than losing data or my identity due to a cyberattack. If my computer hardware fails, I have solid backup protocols which means I can be up and running, business as usual within 24 hours. On the other hand, if my backup systems are attacked, my files could be encrypted, held for ransom, or deleted by a cybercriminal and, I’m no longer in control. Just thinking about that makes my throat go dry. While losing my data scares me, the real tragedy would be having my identity stolen, sold on the Dark Web, and my financial integrity ruined.
Think about all the patient information in your dental practice computer. In addition to the protected health information, there’s personal and financial information. If you experience a cyberattack, imagine the task of patient notification and their reaction to discovery that their protected health and personal information has been compromised.
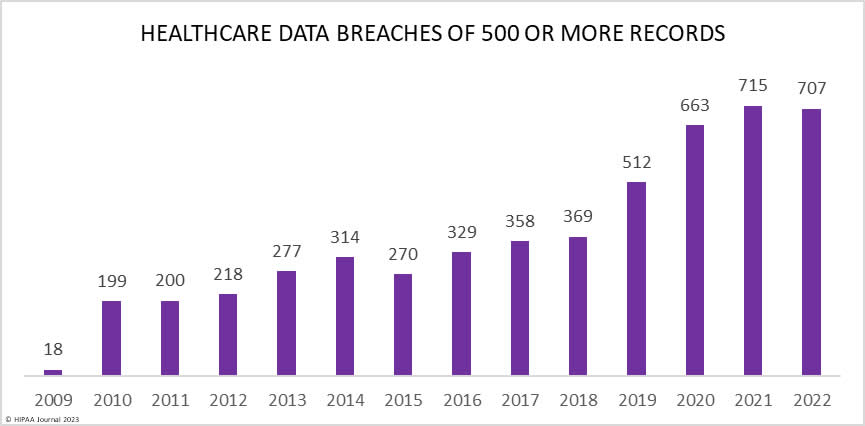
Cybercriminals used the COVID-19 Pandemic to initiate extremely advanced cyberattacks. Healthcare data breaches involving 500 or more records reached their highest levels ever in 2020, 2021 and 2022. There were 11 reported healthcare data breaches of more than 1 million records in 2022 and a further 14 data breaches of over 500,000 records. The majority of those breaches were hacking incidents, many of which involved ransomware or attempted extortion.1
This is why it’s essential for dental offices to ensure that they’re compliant with the latest cybersecurity and data privacy regulations. Amy Wood of Copper Penny Consulting is a cybersecurity and data breach consultant, recommends that dentists hire a local, dental-specific IT provider that provides, supports and knows all security products a dental practice needs. The baseline minimum best practices include: business grade antivirus, patches and updates, business grade, properly configured firewall and backups that meet the 3-2-1 Rule (three kinds of backups, in two different ways, with one of them completely offline).
Next, it is crucial to provide regular privacy and cybersecurity training to employees. Dental practices often overlook federally mandated HIPAA training, others simply provide their team with a copy of the HIPAA Notice of Privacy Practices to read and call that workforce training. This does not help the dental team understand how they can be tricked by phishing and ransomware attacks. Workforce training is the best way to establish your protocols with regards to computer and internet use. Heightened awareness can help the dental team recognize and prevent cybercriminals from successfully accessing your systems.
Here are some of the ways phishing scams work:
- Spoofed emails: Phishers send emails that appear to come from a legitimate source, such as a utility company, delivery company, dental supply company, bank or other financial institution, in order to trick users into providing personal information.
- Business Email Compromise (BEC): This is when the attacker spoofs the sender’s email address to impersonate a business or even a referring dentist’s email in order to get you to click on an attachment. Phishing emails often contain malicious links that, when clicked, install malware onto the victim’s computer.
- Install keyloggers: Keyloggers are a type of malware that records keystrokes and sends them to the attacker. This allows the attacker to gain access to sensitive information such as passwords, credit card numbers, and other confidential data. Keyloggers can be installed on a computer without the user’s knowledge and can be difficult to detect. To protect against keyloggers, users should use strong passwords, install anti-malware software and remain vigilant.
- Fake websites: Phishers create websites that look like legitimate sites, such as a bank or insurance company website in order to trick users into entering personal information.
Another way cybercriminals gain access to computer systems is a technique called social engineering. Social engineering is a type of attack that relies on human interaction to gain access to confidential information or systems. It is a form of manipulation that uses psychological techniques to deceive people into providing sensitive information or performing certain actions. Social engineering attacks can be used to gain access to physical locations, networks, or systems, as well as to steal confidential data or money.
Social engineering attacks could also be phone calls from an imposter posing as a technician from a dental practice management software or IT company. The imposter may call the dental office and ask the front office person to accept a remote access request under the guise of installing an “urgent” security update. Once access is granted malware could be installed.
So what should a dental practice do if they discover they’ve had a cyberattack? The first impulse might be to shut down computers. However, the best step is to keep all computers, servers, and network equipment ON, BUT remove the ethernet cable to disable the internet connection. Remember that you are now in an active crime scene and must respond appropriately to preserve evidence.
Next, involve your IT provider to help you determine the extent of the breach and the type of information that was exposed. Contact your cyber insurance carrier and your HIPAA consultant as soon as possible to walk you through the next steps. Steps include notification of: affected individuals, the U.S. Department of Health and Human Services (HHS), your state attorney general, state or local law enforcement, and in certain cases, the media. If you don’t have a HIPAA consultant, reach out to the Academy of Dental Management Consultants or the Speaking, Consulting Network for names of experts who specialize in HIPAA and cybersecurity. And as with any security incident, be sure to document EVERYTHING.
Here is a link for a HHS Office for Civil Rights PDF A Quick-Response Checklist for Cyberattack: https://www.hhs.gov/sites/default/files/cyber-attack-checklist-06-2017.pdf
COVID-19 has changed many things for dentistry including how we communicate with patients online and conduct business. With the transition to remote work and telehealth, dental offices have had to quickly adapt to new technologies and security measures to protect their data. These measures include enhanced network security, data encryption, and training for staff on cybersecurity best practices. Dental offices should be aware of the increased threat of phishing and ransomware attacks and take steps necessary to protect their data and ensure the security of their patients’ information.
In conclusion, cyberattacks have been on the rise during the COVID-19 pandemic and dental practices must protect themselves from cyber threats. By implementing robust security measures, providing employee training, and having disaster recovery plans in place, dentists can reduce their risk of falling victim to cyberattacks and maintain continuity of care for their patients.
1 https://www.hipaajournal.com/2022-healthcare-data-breach-report/#:~:text=There%20were%2011%20reported%20healthcare%20data%20breaches%20of%20more%20than%201%20million%20records%20in%202022%20and%20a%20further%2014%20data%20breaches%20of%20over%20500%2C000%20records.%20The%20majority%20of%20those%20breaches%20were%20hacking%20incidents%2C%20many%20of%20which%20involved%20ransomware%20or%20attempted%20extortion.
HIPAA Journal. (2023, February 1). 2022 Healthcare Data Breach Report. HIPAA Journal. Retrieved February 15, 2023




